IoT/CPS Steganography: What is it and how does it work?
Can we hide data in the Internet of Things (IoT)? Turns out: yes, we can! In this posting, I briefly summarize some of my own research conducted in last nine years. When we discuss information hiding in the IoT/CPS sector, we need to distinguish at least three different approaches:
- Sending data through the utilized communication protocols (via covert channels).
- Storing data secretly inside the IoT/CPS devices, but without using traditional methods of digital media steganography, such as hiding data inside of images.
- Observing a CPS’ surroundings by exploitation of side channels.
- Storing but also Sending: exploiting low-level actuator states (non-network traffic) to store/transfer secret information
1. Exploiting the Communication Protocols to Send Secret Data
Essentially, the IoT uses TCP/IP-based communication protocols while some more traditional CPS, such as industrial automation systems or building automation systems, use (at least partially) non-TCP/IP protocols, such as BACnet. Data hiding in TCP/IP protocols is not new and several publications already dealt with that topic, see our survey paper (accessible pre-print) for an overview.
However, there are certain specific protocols for the IoT/CPS domain and IoT steganography was already highlighted as a threat by us in 2014. The first research in the domain of CPS steganography that I am aware of was conducted by us and took place in 2011/2012. We have shown that one can embed several different covert channels in the BACnet protocol, which is a highly popular communication protocol for automated buildings around the world. One can exploit unused and reserved header fields in BACnet to signal secret symbols from a covert sender to a covert receiver. However, we also proposed a countermeasure for BACnet-based network steganography in the same paper by deploying a modified BACnet-capable firewall that ensures multi-level security (MLS). Afterwards, several additional papers appeared, especially covering IoT protocols, such as CoAP (paper on CoAP steganography by Mileva et al.) or MQTT (our recent paper on MQTT steganography and its follow-up paper on MQTT 5.0).
2. Storing Data Secretly Inside the Devices
A few years later, we have shown in this paper that one can rather easily store a few bytes of data in i) unused registers of CPS devices (e.g. sensors), and ii) in the state of actuators which then could be observed by a covert receiver. Due to the vitality of CPS, actuator state values are updated on a regular basis either by control logic loops or by human-introduced changes; we applied a device selection strategy to utilize devices which are used the least. To discover suitable CPS components, we used scatter hoarding – a strategy known from Biology. Therefore, we distributed small parts of a steganographic message over a larger number of CPS devices and selected especially these devices for the embedding which are rarely used or not used at all. Overall, it must be noted that the amount of data that can be covertly stored in the CPS is small, e.g. it can contain a message in the size of a cryptographic key within a single smart building, thus limiting the application scenarios for CPS-based information hiding in practice. However, future research might come up with new ideas on how to hide more data in a CPS.
3. Exploitation of Side Channels to Observe Surroundings
Side channels (passive covert channels) can be used to observe the physical environment of a CPS. For instance, in a smart building, one can observe whether a person is present in a particular room.
In my paper „Covert and Side Channels in Buildings and the Prototype of a Building-aware Active Warden” which I already presented at the IEEE Workshop on Security and Forensics in Communication Systems (SFCS) 2012 in Ottawa, I initially spoke about information hiding research for building automation systems. In the remainder I summarize the most important aspects of the paper.
A building automation system (BAS, cf. Wikipedia) is essentially a computer network containing sensors (devices which provide measured values, such as the temperature) and actuators (devices used to control something, like a heating actuator used to control the heating in a room). In other words, BAS are a typical form of CPS.
BAS use various protocols (containing own stacks) and thus make only limited use of TCP/IP. Sometimes they do not utilize TCP/IP-based protocols at all. My work essentially applies to different types of CPS, such as industrial control systems, too.
The question I wanted to answer is: Are Covert or Side Channels Possible in BAS Environments? Indeed, the answer for both questions is “Yes”.
To differentiate between both terms, I refer to a side channel as a communication channel without an intentional sender while a covert channel requires an intentional sender. This distinction is relatively common in the current covert channel research community.
Exploitation of Side Channels in BAS (and other Types of CPS)
A side channel in a building automation systems exists if a user can obtain information leaked by the BAS network. Therefore, the user can monitor the BAS network for messages or can request information from sensors. While the first scenario is a passive side channel, the latter one is an active side channel.
Example use-case: An employee wants to steal a document from the manager’s office. Indeed, the employee wants to ensure that the manager is currently out of his office, i.e. he wants to make sure that it is safe to steal the document without getting caught.
The employee utilizes the BAS to obtain information about the presence of the manager in the room. Therefore the employee can request sensor information (e.g. temperature, lighting …) that describe the current situation in the manager’s office. If the lightning is turned off, if the temperature does not seem to represent the presence of a person in the room and if the heating is turned off, the employee can be relatively sure that the office is empty and that it is safe to steal the document at the moment. I consider such unintended information transfer as a side channel of the BAS (CPS).
4. Sending Through Low-level Covert Channels in Building Automation Systems
For a covert channel communication, it is necessary to have an intentional sender in the scenario. Let us therefore imagine a situation in which we have a building with two rooms as shown in Fig. 1.
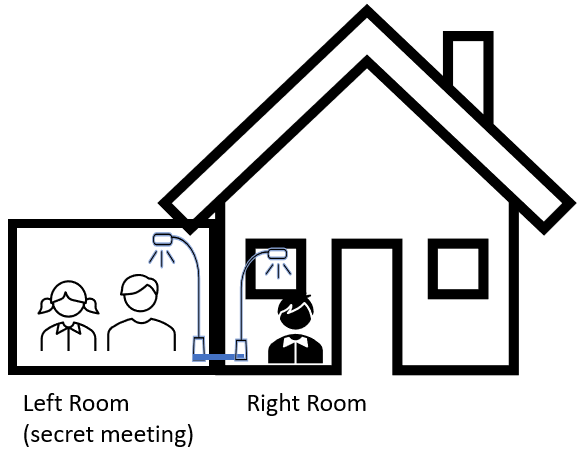
Fig. 1: A Sample Covert Channel Scenario for a Building Automation
System.
In the remainder I will show how above-mentioned works can be combined: The left room is closed and any network access in the room is deactivated. A secret meeting is taking place in the room and the results of the meeting have to be kept secret until the meeting is over. The security policy of the organization prevents any communication from the left (secret) room to the right (public) room.
We assume that one person in the left room is a whistleblower wants to pre-inform a person in the right room about the estimated result of the secret discussion. Therefore, the BAS can be manipulated. The whistleblower in the left room could turn on the light in the left room (“because it is getting dark outside”). Now, the person in the right room could simply request the status of the lightning in the left room to determine the outcome of the meeting. Alternatively, the light button in the left room could be connected to an additional device by the BAS logic and could turn on the lightening in the right room (or any other device in the building) at the same time to signal hidden information. This covert channel is shown in Fig. 2. One scenario for such an exploitation would be the pope election – an insider could reveal the election’s result before the official disclosure. Additional scenarios can be found in the already mentioned SFCS paper.
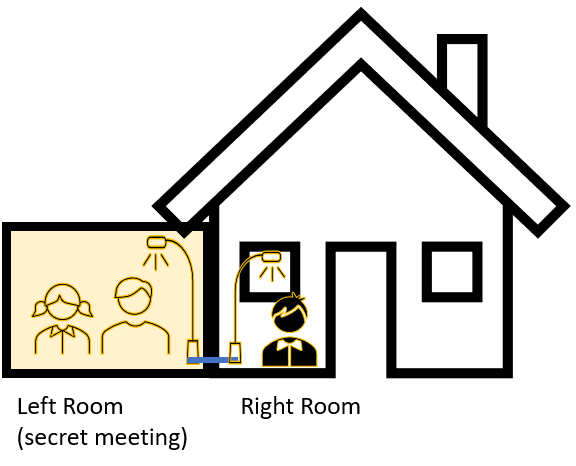
Fig. 2: A covert channel established in the BAS that breaks the security policy of the building.
Thus, covert channels can leak hidden information and can break security policies in building environments. The details can be found in my referenced paper above.
Preventing Covert and Side Channels
In above-mentioned paper, we also present a technique to prevent at least a subset of the possible covert and side channels in BAS. I therefore route all BAS commands of applications (e.g. smart phone applications used to control or monitor the building) through a middleware that contains multilevel security (MLS) and role-based access control (RBAC) support. Low-level prevention means are part of future work.
List of references linked above
-
Mileva A, Velinov A, Hartmann L et al (2021a) Comprehensive analysis of MQTT 5.0 susceptibility to network covert channels. Computers & Security 104:102207. Elsevier, DOI: https://doi.org/10.1016/j.cose.2021.102207
-
Velinov A, Mileva A, Wendzel S, Mazurczyk W (2019a) Covert channels in the MQTT-based internet of things. ACCESS 7:161899–161915. IEEE, DOI: 10.1109/ACCESS.2019.2951425
-
Mileva, A, Velinov, A, Stojanov, D (2018) New Covert Channels in Internet of Things. In: The 12th International Conference on Emerging Security Information, Systems and Technologies - SECURWARE 2018.
-
Wendzel S, Mazurczyk W, Haas G (2017d) Steganography for cyber-physical systems. Journal of Cyber Security and Mobility (JCSM) 6:105–126. River Publishers, DOI: 10.13052/jcsm2245-1439.621
-
Wendzel S, Zander S, Fechner B, Herdin C (2015a) Pattern-based survey and categorization of network covert channel techniques. ACM Computing Surveys (CSUR) 47:1–26. ACM New York, NY, USA, DOI: 10.1145/2684195
-
Wendzel S, Mazurczyk W, Caviglione L, Meier M (2014a) Hidden and uncontrolled–on the emergence of network steganographic threats. In: ISSE 2014 Securing Electronic Business Processes. Springer, pp 123–133, DOI: 10.1007/978-3-658-06708-3_9
-
Wendzel S, Kahler B, Rist T (2012b) Covert channels and their prevention in building automation protocols: A prototype exemplified using BACnet. In: 2012 IEEE International Conference on Green Computing and Communications (GreenCom), Internet of Things (iThings) and Cyber-physical Systems (CPSCom). IEEE, pp 731–736, DOI: 10.1109/GreenCom.2012.120
-
Wendzel S (2012g) Covert and side channels in buildings and the prototype of a building-aware active warden. In: 2012 IEEE International Conference on Communications (ICC). IEEE, pp 6753–6758, DOI: 10.1109/ICC.2012.6364876
Updates:
- 2021-Feb-24: Modified the content for better reliability and merged two different postings into one.